Introduction
IPTV Data Transmission is the backbone of modern digital TV delivery over IP networks. From the moment a user presses “play” to the instant frames appear on screen, IPTV data transmission orchestrates a symphony of packets, protocols, contraction, buffering, and network design. In this composition, we will explain how IPTV data workshop, explore IPTV streaming technology, examine IPTV data contraction and IPTV bandwidth conditions, compare IPTV network protocols and multicast vs unicast strategies, address IPTV softening issues, and eventually bandy IPTV data encryption.
How IPTV Data Works
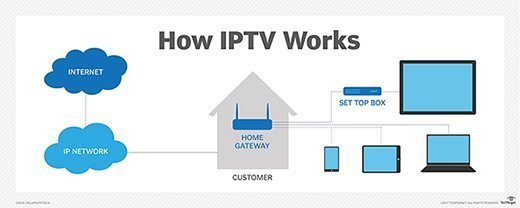
At its core, IPTV(Internet Protocol Television) transforms videotape and audio content into IP packets to be delivered over broadband networks. Originally, source content is captured and decoded into a digital format. Next, via garbling and packetization, the content is divided into lower gobbets — packets — each carrying a title, sequence number, and cargo.
During this inflow, IPTV uses the Internet Protocol( IP), frequently counting on multicast delivery when numerous users view the same content, or unicast delivery for on-demand content or when multicast isn’t possible. The packets travel along network routes following routing tables and switching opinions.
IPTV Streaming Technology
IPTV streaming technology integrates several layers: happy accession, garbling, middleware, delivery networks(CDN, backhaul, access), and customer bias.
- Content accession captures live television, VOD, or catch-up services.
- Encoding and transcoding convert raw videotape into compressed formats ( e.g., H.264, H.265, HEVC).
- Middleware and control manage stoner authentication, EPG( electronic program guide), channel switching, and session control.
- Streaming waiters originate waiters, host aqueducts, and distribute to edge waiters or CDNs.
- Distribution network/ CDN caches are happy near end users to reduce latency.
Throughout this chain, protocols like HTTP, RTP, RTSP, and MPEG- gusto play a role in delivering content. Adaptive bitrate streaming( e.g., ABR) enables guests to switch among quality levels to match bandwidth swings.
IPTV Data Compression
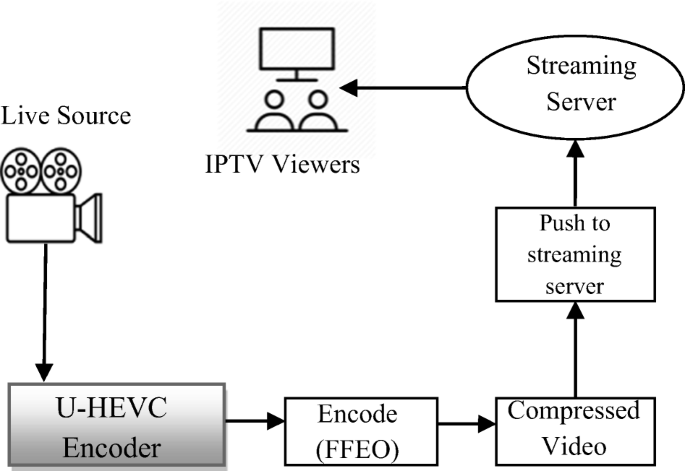
Compression is essential because raw videotape is enormous in size. To transmit efficiently, IPTV systems use lossy videotape contraction. The end is to reduce the bitrate while conserving perceived quality.
- Intra-frame contraction (within a single frame, e.g., I frames) eliminates redundancies inside that frame.
- Inter-frame contraction (between frames, e.g., P frames, B frames) encodes just the differences.
Advanced codecs use stir estimation, transform rendering, quantization, entropy coding, and more. The advanced the contraction, the lower the bitrate demanded, but also the lesser the computational complexity and eventuality of vestiges.
IPTV Bandwidth Requirements
One of the critical challenges in IPTV is matching bandwidth conditions to gladden quality and stoner demand.
- Standard description( SD) aqueducts may bear 2 – 5 Mbps
- High description( HD) aqueducts frequently need 5 – 8 Mbps
- 4K/ Ultra HD may demand 15 – 25 Mbps or further, depending on contraction effectiveness and content complexity
However, providers must allocate above for packet heads, error correction, and headroom for bursts. Also, when numerous druggies sluice contemporaneously, aggregate bandwidth must be gauged.
IPTV Network Protocols
The protocols used in IPTV support signaling, streaming, and control. Important bones
include
- RTP(Real-time Transport Protocol): Is frequently used for real-time delivery, generally combined with RTCP for control( timing, statistics).
- RTSP(Real-Time Streaming Protocol): For controlling playback( play, pause, teardown).
- HTTP/ HTTPS/ TCP: In ultramodern IPTV and ABR systems( e.g., MPEG-DASH or HLS), content is delivered over HTTP.
- UDP: For low- low-quiescence streaming, especially in multicast scripts, where minor packet losses are respectable.
Therefore, IPTV network protocols coordinate session setup, content delivery, timing, error monitoring, and multicast operations. Understanding the SE protocols is essential for network specialists designing IPTV systems.
IPTV Multicast vs Unicast

One of the vital architectural opinions is whether to deliver content via multicast or unicast( or mongrel)
- Multicast: A single sluice from garçon to multiple donors. Effective for live television channels where numerous viewers watch the same content. Network-level multicast replicates packets only when demanded.
- Pros: Scales well, saves bandwidth across the core network.
- Cons: only work when network bias (routers, switches) support multicast, are less flexible for on-demand content, and harder to cut across disciplines on the internet.
- Unicast: Each stoner gets a separate sluice(one-to-one).
- Pros: Simpler to implement over the public internet, flexible(on-demand, substantiated aqueducts).
- Cons: Bandwidth scales linearly with druggies; hamstrung for numerous druggies watching the same channel.
Numerous IPTV systems employ a mongrel approach, multicast for live channels within controlled network disciplines, and unicast/ HTTP- grounded streaming for VOD or fallback scripts.
IPTV Data Encryption
Security and content protection are pivotal in IPTV, especially for decorative content. IPTV data encryption prevents unauthorized access, piracy and ensures the rights operation. crucial ways include.
- DRM( Digital Rights Management) Systems like Widevine, PlayReady, and Apple FairPlay manage license keys, decryption rights, and apply operation programs.
- AES Encryption is frequently used to cipher videotape parts( e.g., AES-128 in HLS), where each member is translated with AES and delivered over HTTPS.
- TLS/ SSL Secure the transport subcaste (HTTPS) to help man- in- the- middle attacks.
- SRTP (Secure Real-time Transport Protocol) adds encryption, communication authentication, and integrity to RTP channels.
- Authentication/ Authorization Before decryption, guests must validate rights using usernames, credentials, or instruments.
Therefore, IPTV data encryption ensures that only valid and sanctioned guests can decipher and view the content, securing the content provider’s profit and consumer trust.
Conclusion
To sum up, IPTV Data Transmission embodies the art and wisdom of delivering TV over IP networks. By understanding how IPTV data workshop, the streaming technologies, contraction ways, bandwidth requirements, network protocols, the differences of multicast vs unicast, softening risks, and data encryption, one earnings deep insight into what makes IPTV systems crack.

